
Ransomware attacks double in cost moving into 2020
Average ransomware costs shot up 104% to over £64,000 ($84k) in Q4 2019 from £31,500 ($41k) in Q3 2019.
Recent research from ransomware recovery specialists Coveware concludes the average cost of ransomware attacks throughout the last quarter of 2019 was more than twice that of the preceding quarter. This is predominantly due to significant increases in the popularity of the Ryuk and Sodinokibi (REvil) strains.
The report, known as the “Ransomware Marketplace report” uses anonymous ransomware data collected from its database of cases resolved by its Incident Response Platform. Among the factors used to calculate these costs are:
- Ransom payment (if made)
- Remediation of network and hardware
- Lost revenue
- Brand damage (if business interruption is severe enough)
Average ransomware payouts

Another concern is the proliferation of ransomware attackers exporting sensitive data and using the threat of its release as leverage for faster and larger payouts. This introduces the potential additional costs from 3rd party claims over data breaches.
Downtime continues to rise
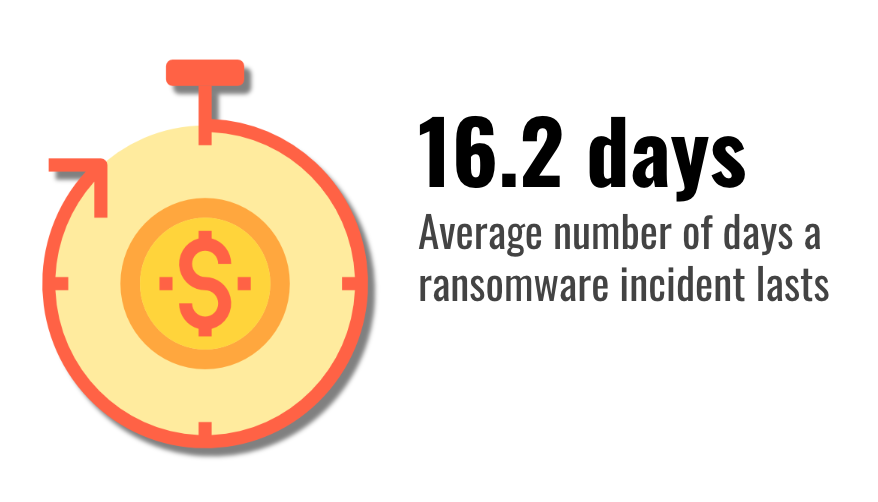
As mentioned above, a significant factor during any ransomware attack is the downtime they cause for organisations. The average downtime for organisations hit by ransomware attacks has risen 34% to 16.2 days in Q4 from 12.1 days in Q3.
A pertinent example of how downtime can affect an organisation is the Wannacry attacks of 2017, which hit the UK’s National Health Service (NHS) the hardest. The NHS was affected at 81 of it’s 236 trusts across England, causing over 19,000 cancelled appointments, 200,000 locked computers and around £92 million in damages and upgrades.
Who is a target?
There are many organisations that hold the belief they are too small to be targeted by ransomware attacks. Unfortunately, the report which measured the average size of organisations hit by the top three most prevalent ransomware strains, revealed that there is not really a minimum size.

How the ransomware attacks begin

A huge attack vector, specifically for the Ryuk strain, was phishing emails. The relative ease and ability to scale phishing campaigns, and readily available data with which to conduct highly targeted spear phishing attacks makes this vector particularly attractive. Couple this with the average ransom from each strain (pictured below), and the ability to spot phishing emails becomes less of a luxury and more of an absolute necessity.

How to avoid becoming a victim?
We have already looked at how to protect yourself and your organisation against ransomware attacks in a previous article. However, as eluded to earlier, one of the most important factors is user knowledge. Security hardware will let a phishing email through at some point, this is fact. When this happens, it is the individual user’s knowledge that will determine whether the email is spotted and reported, or if it is clicked, potentially starting a crippling ransomware infection in your organisation.
Regular Security Awareness training and Simulated Phishing exercises keep your users in a security-first mindset. This dramatically reduces their susceptibility for falling for a phishing attack.
At Phishing Tackle, we went as far as to create a free tool which determines how many of your users are currently susceptible to a phishing attack. You can find it here: Free Click-Prone® Test.
Take action as soon as possible, malicious actors go after any targets they believe will fall for their phishing campaigns. The less training users have, the more likely they are to fall for these attacks.

