
Tesla vulnerability: Knowing The Risks of MitM Attacks
Tesla accounts could be compromised via a Man-in-the-Middle (MitM) phishing attack, as revealed by researchers. This vulnerability allows threat actors to access Tesla cars, unlock, and start them.
Tesla’s phone key system has a weakness that hackers exploited. They generated a fake phone key by taking use of a bug in the car software (11.1 2024.2.7) and the Tesla app (4.30.6). This fake key could then be used to unlock and steal Tesla automobiles.
Tommy Mysk and Talal Haj Bakry alerted Tesla to the vulnerability of using a new phone as a key due to its lack of solid authentication. However, Tesla denied their findings, claiming that the investigation was out of scope. Tesla believed that the vulnerabilities were unrelated to their present security focal point, even though the researchers’ worries were clear.
Attackers can exploit this vulnerability, providing unauthorized access through the Tesla app if they possess the proper login information and phone key. This implies attackers could unlock the car and drive away while using another person’s phone.
Hackers exploit Tesla’s vulnerabilities using deceptive Wi-Fi tactics
Researchers that specialise in security issues caution that attackers could be able to take your Tesla by phishing for your login information. The Man-in-the-Middle (MitM) attack exposes Tesla account information on a fake website.
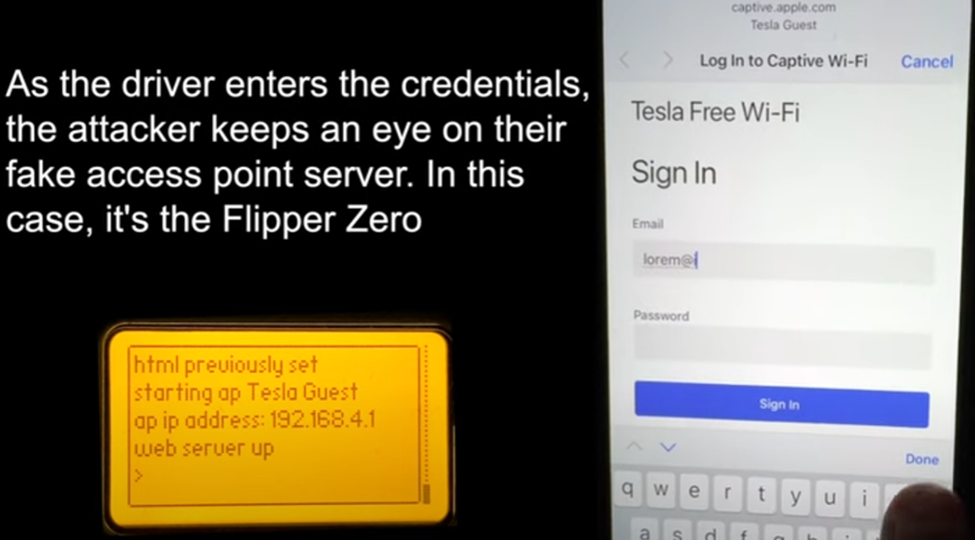
Hackers set up hunt at Tesla charging stations with the goal of causing mischief by creating the “Tesla Guest” Wi-Fi network. One of the most common places for Tesla drivers to see this misleading SSID is at their charging stations.
Flipper Zero, a multifunctional open-source device for hardware probing, firmware flashing, debugging, and fuzzing, enables hackers to create and manipulate these networks. Furthermore, any device capable of creating a Wi-Fi hotspot can be used for similar purposes.
Upon connecting to the deceptive network, users are prompted to input their account credentials on a fake Tesla login screen. Any data entered on this phishing website is instantly accessible to the attacker via the Flipper Zero device.
The phishing page asks users to provide a one-time password, which allows hackers to bypass two-factor authentication. As a result, the attackers must act quickly to get access to the Tesla app they control before the password expires.
Once unauthorised access is achieved, attackers can actively track the location of a hacked Tesla in real time. They may then use this information for their benefit later, including registering a new phone key to open and drive away with the compromised car.
Phone Keys use Tesla’s mobile app to easily sync with the car owner’s smartphone. This unique device automatically locks and unlocks the car via a secure Bluetooth connection.
Additionally, Tesla vehicles use Card Keys, which are thin RFID cards that need to be inserted into the RFID reader located in the centre console for the car to start. When the Phone Key is not accessible or runs out of battery, Tesla considers that these physical cards are a backup option that may be used in its place. Card Keys provide Tesla owners a sense of ease with their improved security features.

The car’s screen does not notify the owner that a new Phone key has been produced, therefore the owner is still uninformed that the car is vulnerable to theft and hacking. Researchers propose a method that combines the physical Tesla Card Key with the phone key to mitigate the hacking issue.
The suggested procedure calls for putting the RFID card on the interior of the vehicle’s central console’s RFID reader to start the engine. Tesla emphasises that the authorised way to unlock and start their vehicles is to use the Phone Key in its intended configuration. It’s noteworthy that adding the RFID card to the Phone Key is not required according to the Tesla Model 3 manual.
Phishing attacks are on the rise, and it is important to protect your organisation. One effective way to do this is by increasing user awareness about these types of attacks. Phishing Tackle is a great resource that can help you in this regard. They offer a free 14-day trial to help train your users to recognise and avoid phishing attacks.

