
Phishing URL to give you nightmares
As reported on Reddit just a few days ago, here is a heads-up to a URL that could be troublesome, courtesy of a genuine Adobe domain redirect.
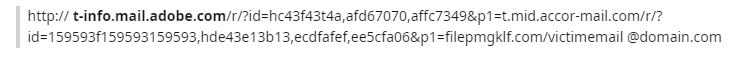
On first glance, it seems to be legitimate because it ends with adobe.com, but if you look more closely at the whole query string you will see it has “hidden” secrets. This link actually takes the follower to a fake Office 365 landing page hosted on Windows.net.
On closer inspection (and a little playing around), it seems you can put anything after the “&p1=” query parameter and Adobe will redirect you. We think you’ll agree this is rather concerning.

Looking further down the original URL, there are actually using THREE redirects – Adobe, a server owned by the Accor hotel group, and finally a server hosted by the scammers. The landing page – on windows.net – then submits your credentials to a compromised WordPress site at 5beauty.ru.
The sysadmin who discovered this has diligently reported it to Adobe and Microsoft, and sent messages to addresses at Accor and the 5beauty site. They have also reported the “filepmgklf” domain to the registrar and site host, as it appears to be owned by the scammers.
It’s getting harder and harder to spot this stuff so continuous training and awareness is critical in helping keep your organisation secure.

