
LastPass developer systems were compromised, providing access to source code
LastPass, a password manager, was compromised recently. Threat actors will be able to steal the company’s source code and confidential technical knowledge because of this.
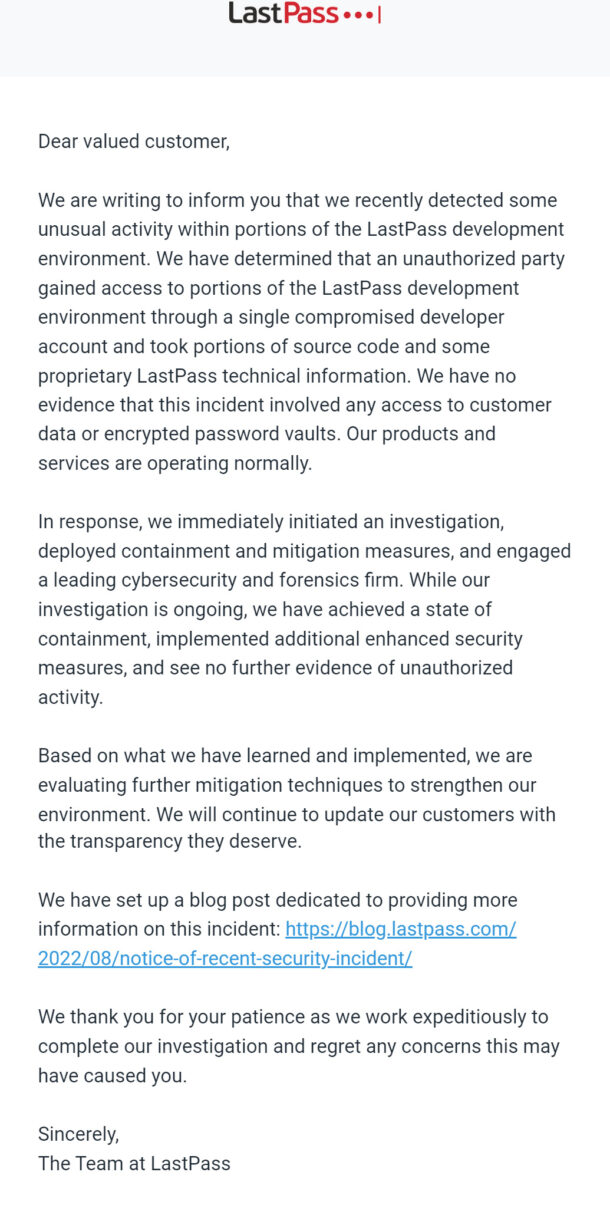
It was revealed by insiders that when LastPass was compromised, employees were trying to stop the attack. The company issued a security alert revealing that the organisation had been compromised by a developer account that had been exploited to get into the developer environment.
Threat actors did obtain some of LastPass’s source code and “Proprietary LastPass technical material,” although the company claims that there is no proof that user data or encrypted password vaults were stolen.
According to LastPass CEO Karim Toubba:
We have implemented containment and mitigation strategies in response to the attack, as well as hired a reputable cybersecurity and forensics company. While our investigation is ongoing, we have reached a state of containment, put more, stronger security measures in place, and we have not seen any new indications of unauthorised activity.
The CISO of SafeBreach, Avishai Avivi, discussed the potential long-term consequences of the source code theft. He continued by saying:
Bad actors will want source code for the same reason bank robbers will want floor plans to a bank. Being able to understand how the particular software works can potentially help the malicious actor identify its weak points and ways of gaining entry.
This doesn’t, however, mean that access to the bank’s floor plan, or even being able to compromise one of the bank employees, necessarily means that any money will be stolen.”
Avishai Avivi – CISO, SafeBreach
Customers’ passwords are kept in LastPass’ encrypted vaults, which can only be unlocked with the master password. Since the vault doesn’t save the master passwords, as part of LastPass’ Zero Knowledge security architecture, the master passwords weren’t hacked.

In the case of your master password and the information kept in your vault, zero knowledge implies that only you have access to them. A credential stuffing attack, which PBKDF2 hashing from the flowchart above is meant to prevent, was suggestively employed against LastPass in late 2021.
Regarding the incident, how the threat actors got access to the developer account, and what source code was taken, LastPass has not provided any more information. You can read the whole security warning that was delivered to users below.
According to the company, over 33 million users and 100,000 businesses use LastPass, making it one of the biggest password management firms in the world. Customers and companies use the software provided by the firm to store their passwords safely, but there are always worries that if the company were to be hacked, malicious actors would gain access to the credentials.
Users of LastPass should be alert, keep up with current events, and monitor their accounts for any erratic activity or login alerts. The usage of an authenticator app to protect logins is one of the many MFA options that LastPass offers, and it is extremely crucial to enable them all.
Enabling multi-factor authentication on your accounts is essential for reducing your susceptibility to threat actors accessing your account even if your password is hacked.
Has your organisation started to increase cyber security measures yet? Start your two-week free trial today.

